Description
Scout2 is an open source tool that helps assessing the security posture of AWS environments. Using the AWS API, the Scout2 Python scripts fetch CloudTrail, EC2, IAM, RDS, and S3, configuration data. The gathered configuration is analyzed and stored as JSON objects in several JavaScript files. These files are imported in the Scout2 HTML report, which allows for a quick and efficient review of the AWS configuration. Scout2 ships with over thirty rules, and can easily be extended to support more services and test cases.
HTML Report
The Scout2 Python script populates JavaScript variables displayed in the HTML report. In addition to displaying the AWS configuration, the AWS Scout2 HTML report highlights high-risk areas automatically. Potential findings are highlight with two different colors
- red :: danger
- orange :: warning
EC2 view
Security Groups are the first layer of defense for EC2 instances (AWS documentation), and control both inbound and outbound traffic at the instance level. AWS Scout2 has a default ruleset that reports known sensitive ports that are open to the Internet (in the following screenshot, 22/SSH). Additionally, the default ruleset also reports open ports whose number are associated with plaintext protocol (in the following screenshot, 23/Telnet).
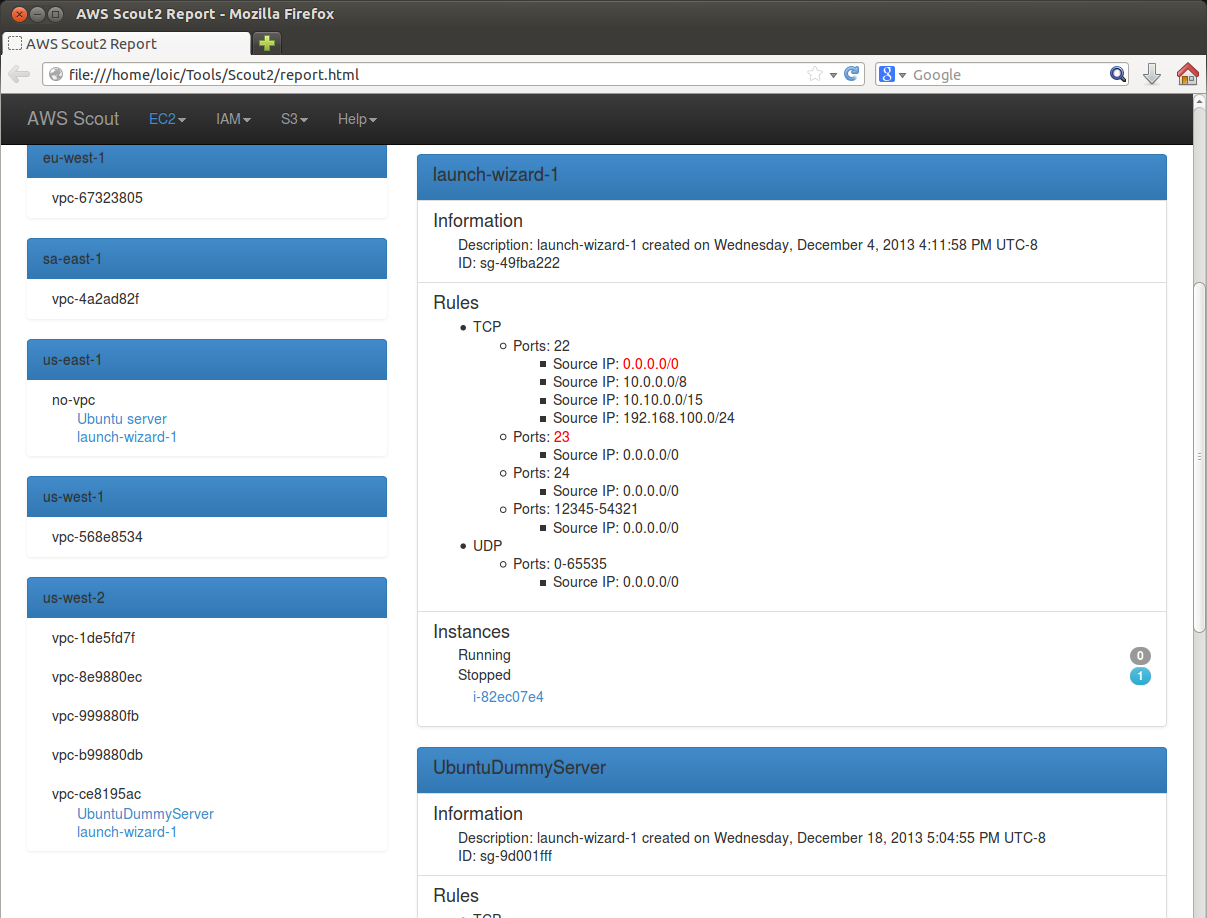
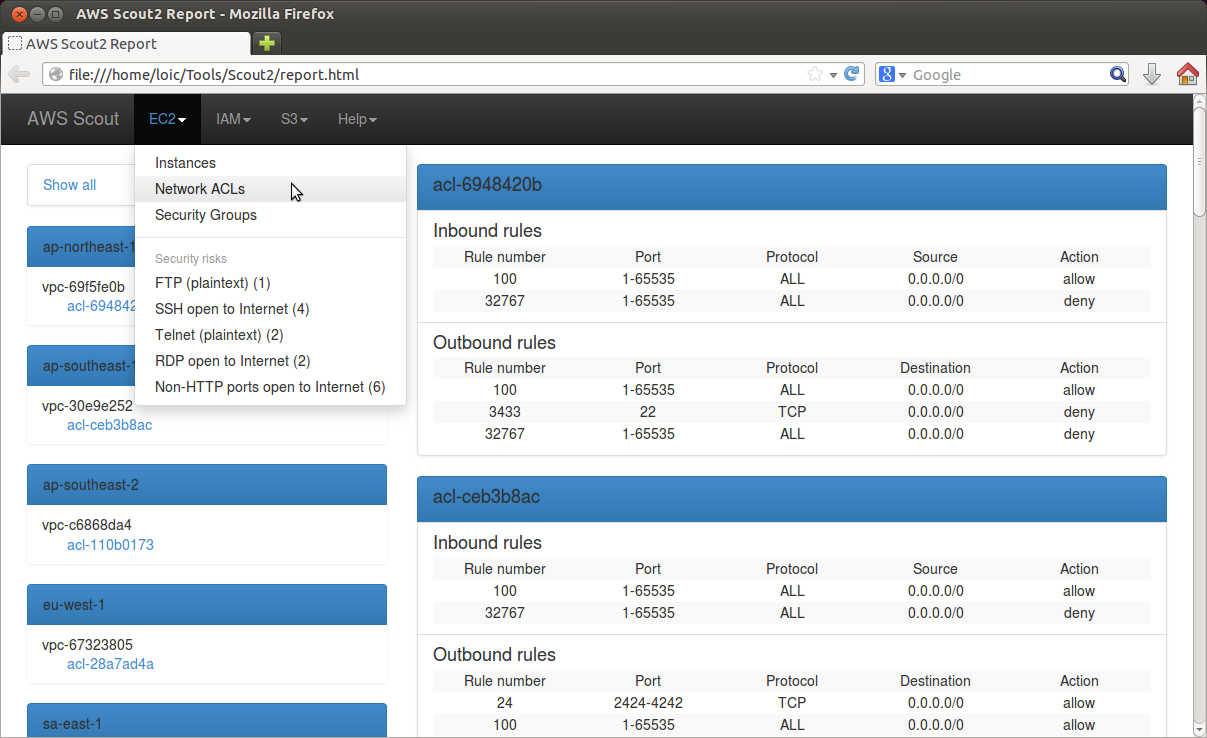
Network ACLs are the second layer of defense, and control traffic in and out of a subnet. AWS Scout2 has an EC2/Network ACLs view that reports all existing rules:
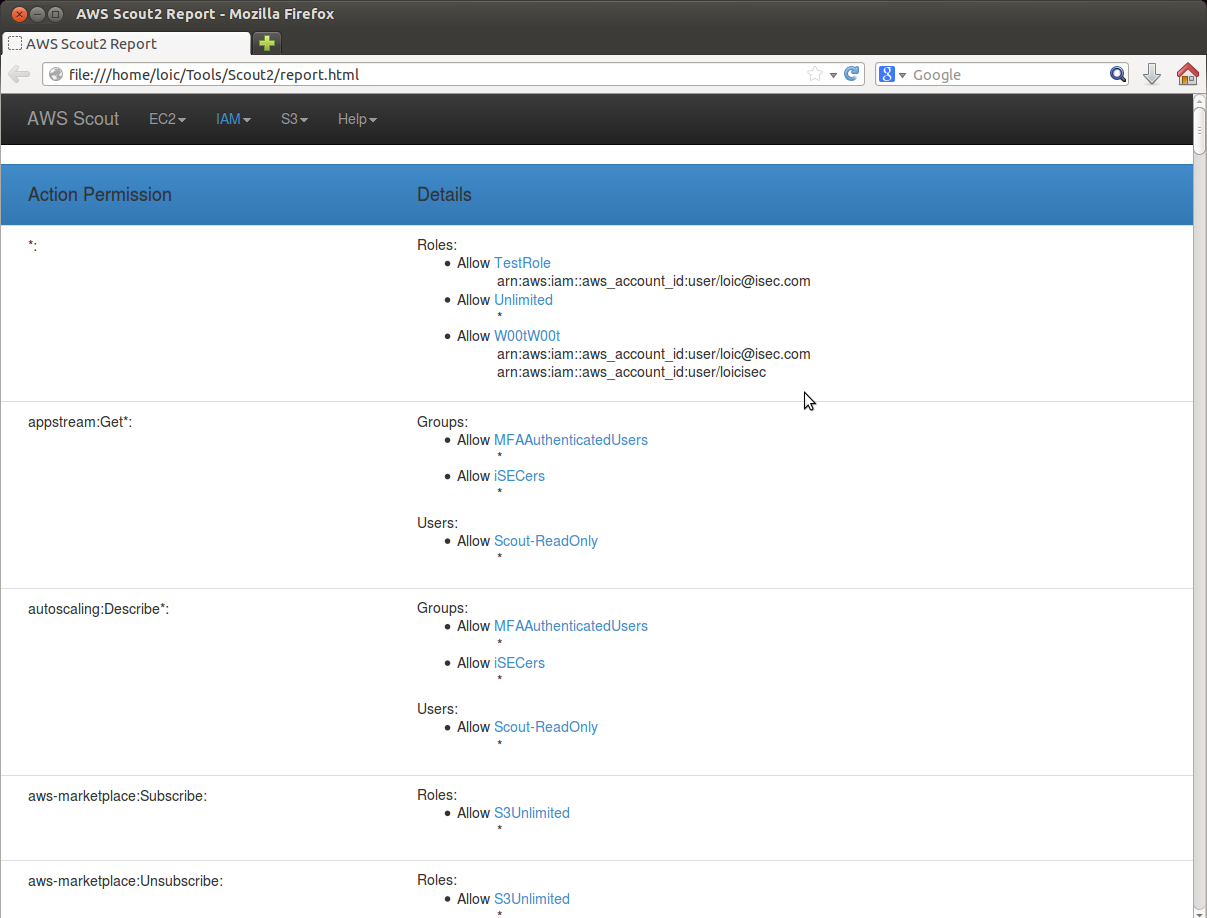
IAM view
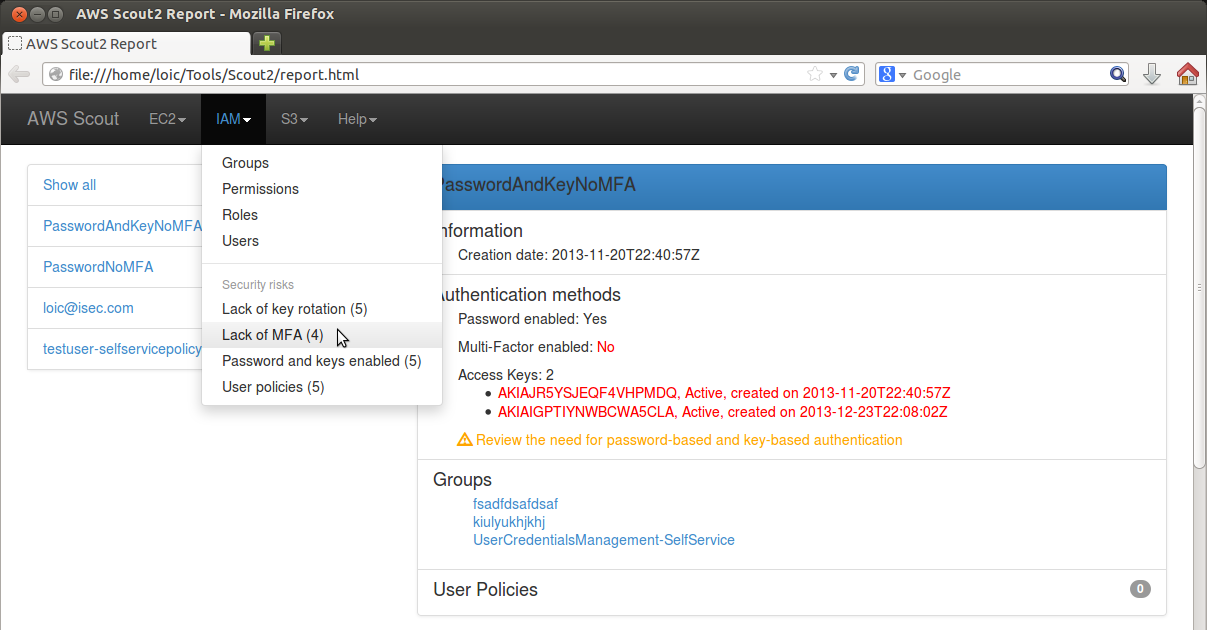
The IAM tab in the HTML report allows to review IAM users, groups and roles. In the following screenshot, AWS Scout2 reports two dangerous findings (lack of Multi-Factor Authentication, lack of access-key rotation), and warns about a third one (support for two types of authentication).
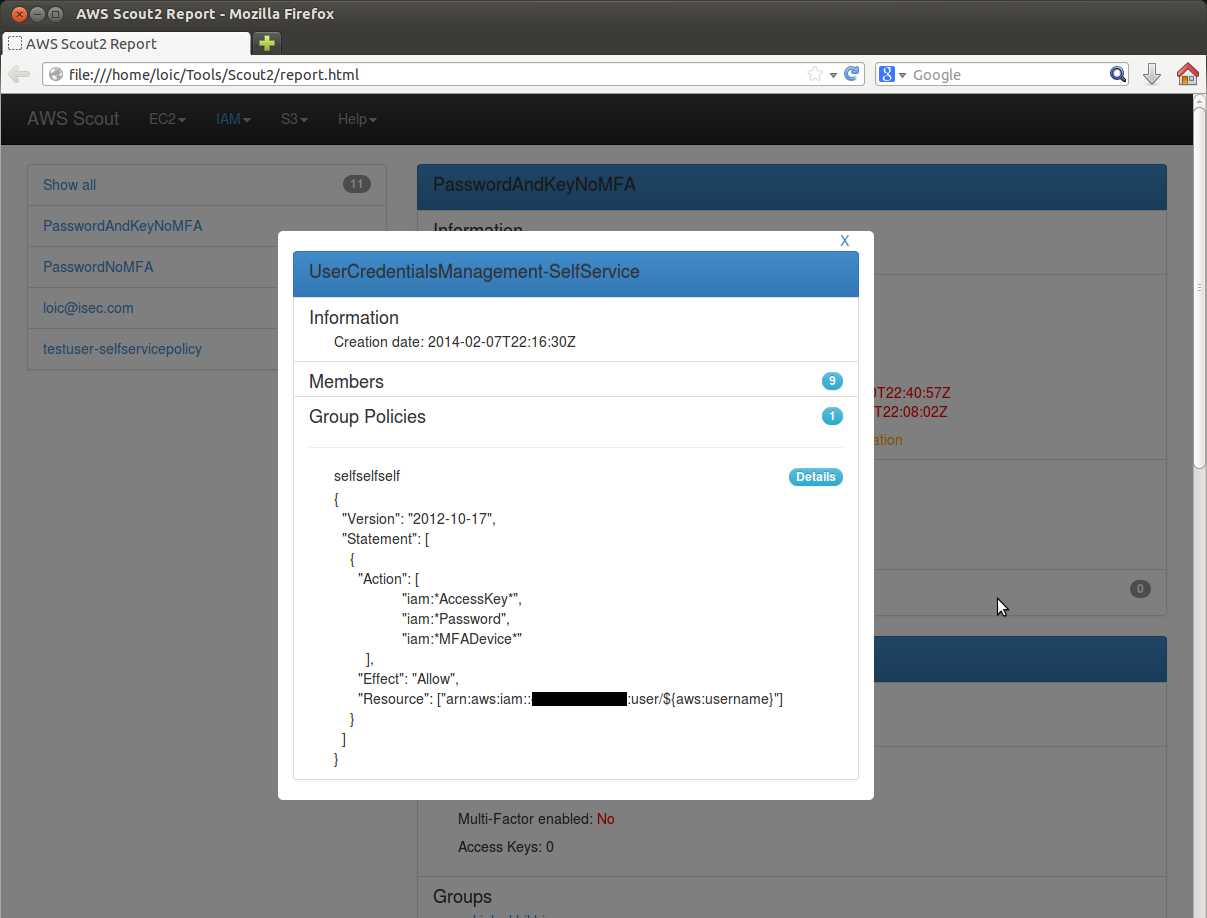
When reviewing IAM users' settings, you can access details about IAM groups they belong to by clicking on the name of the group. This will overlay the IAM group details, including policies and other members.
The IAM view also offers a permission summary that lists all permissions that are granted, or denied, throughout the AWS account policies. For each permission, a list of IAM users, groups and roles is provided, along with the resources accessible to each of them.
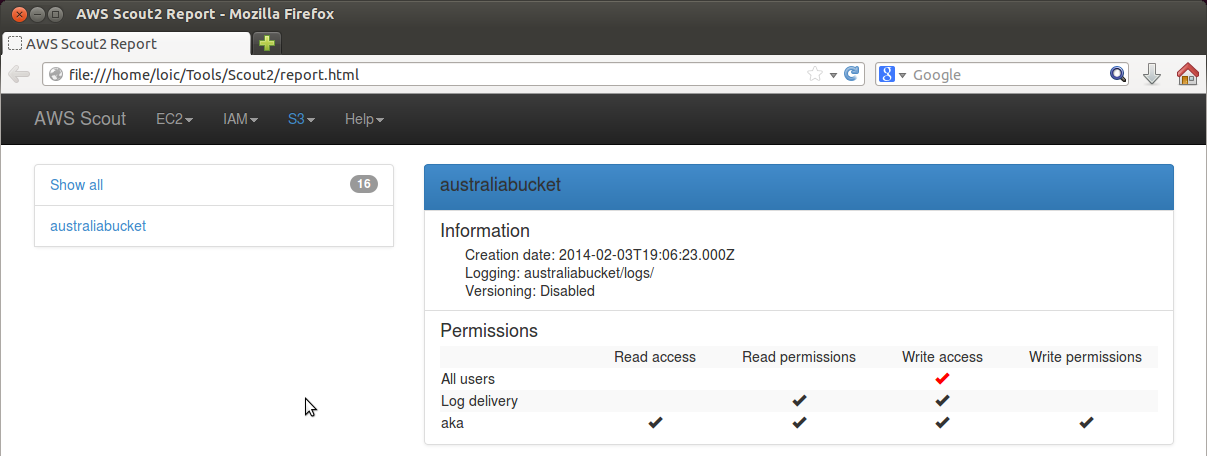
S3 view
AWS Scout2 fetches the S3 configuration as well. The default ruleset highlights buckets that are world-writable, and whose permissions are world-writable. Additionally, a warning is displayed for world-readable buckets.
Default rulesets
AWS Scout2 comes with the following default rulesets:
EC2 default ruleset
| Description | Level |
|---|---|
| Sensitive port open to the Internet (e.g. SSH, RDP, SQL, ...) | danger |
| Plaintext-protocol port open (e.g. FTP, Telnet, ...) | danger |
| Non-HTTP ports open to the Internet (not 80/443) | warning |
| Lack of network ACLs (Inbound) | warning |
| Lack of network ACLs (Outbound) | warning |
IAM default ruleset
| Description | Level |
|---|---|
| Lack of key rotation | danger |
| Lack of (inactive) key rotation | danger |
| Lack of Multi-Factor Authentication | danger |
| Password and Access Key authorized for a given account | warning |
| Existence of user policy | warning |
S3 default ruleset
| Description | Level |
|---|---|
| Bucket world-writable | danger |
| Bucket's permissions world-writable | danger |
| Bucket world-readable | danger |
How to create a new rule
Directions
- Open the default ruleset you wish to enhance, and create a new entry.
- Define and implement the new callback in the corresponding utils file.
- Update the report.html to highlight thew new finding.
Example
The following code snippets illustrate the addition of a new rule. In this example, the new rule warns against the use of user policies (this rule is now part of the default ruleset).
git diff rules/findings-iam.default.json:
+ },
+ "user-policy": {
+ "description": "User policies",
+ "entity": "users",
+ "callback": "hasUserPolicy",
+ "callback_args": "",
+ "level": "warning"
+ }
git diff AWSScout2/finding_iam.py:
+
+ def hasUserPolicy(self, key, obj):
+ if len(obj['policies']) > 0:
+ self.addItem(obj['user_name'], obj['user_name'])
git diff report.html:
- <h4 class="list-group-item-heading">User Policies <spcan class="badge pull-right">{{count policies}}</span></h4>
+ <h4 class="list-group-item-heading">User Policies <span class="badge pull-right" id="iam_users-user-policy-{{user_name}}">{{count policies}}</span></h4>
Authors and Contributors
- Loic Simon - @l01cd3v